ToCToU를 이용한 검증 로직 우회하기(SSRF/OOB/XXE/ETC)
⚠️ SSRF에 관련된 내용은 Cullinan > SSRF에서 관리하고 있습니다. ToCToU를 포함하여 최신 데이터로 유지되고 있으니 참고 부탁드려요!
What is ToCToU?
ToCToU는 Time Of Check to Time Of Use의 약자로 시간차를 이용한 공격이며 보통 Race condition attack에서 많이 나오던 개념입니다. 별 내용은 없지만 예전에 toctou 관련 글을 쓰긴 헀었네요.
간단히 풀어서 설명하면 이렇습니다.
- A서비스는 사용자로부터 받은 데이터를 B라는 함수로 문제가 있는지 검사하고, C라는 함수로 등록
- 이 과정에서 B와 C사이에는 시간차가 존재할 수 있음
- 그 시간차이 내에 사용자로 부터 받은 데이터를 변경할 수 있다면 B 검사 로직의 input과 C 등록 함수의 input을 다르게 줄 수 있음
- 그러면 보안성을 위해 적용한 B 함수가 무력화 되기 때문에 다른 취약점으로 연결될 수 있는 포인트가 됨
보통의 경우 B와 같은 검사 함수와 C와 같은 처리로직/비즈니스 로직은 가까운 위치에 있어 시간 차이가 거의 나지 않지만 로직,정책,코드 등의 특이사항으로 B와 C사이의 간격이 벌어지는 경우가 있습니다. 이 틈새를 공격자가 인지했다면 위에서 이야기드린대로 검사 함수를 무력화할 수 있는 방법이 됩니다.

Bypassing protection
보통 ToCToU는 시스템 해킹 기법으로 많이 알려져 있지만, 원리 자체는 충분히 웹 해킹에도 이용될 수 있습니다. 몇가지 예시를 통해 가볍게 설명해볼게요. 제가 위에서 이야기드린 조건은 시간 차이가 있을 때 사용자 입력을 변경이 가능한지 여부입니다.
이 조건을 충족할 수 있는 것 중 하나가 DNS Record입니다. DNS Record는 도메인 소유자가 언제든지 변경할 수 있으며, 상황에 따라 다르겠지만 보통 30분 이내로 A Record, CNAME 등 DNS 정보에 대해 변경이 가능합니다. 그 말은 곧 URL/Domain에 대한 검증과 실행하는 구간의 차이가 어느정도 벌어지는 경우 DNS Record 수정을 통해 악의적인 행위가 가능하다는 것입니다.
이 때 검사하는 로직과 웹 접근하는 기능의 시간차보다 DNS Record 수정이 반영되는 시간 차이가 짧아지는 경우 검사 로직과 웹 요청 처리 로직의 최종 목적지 IP를 우회할 수 있습니다.
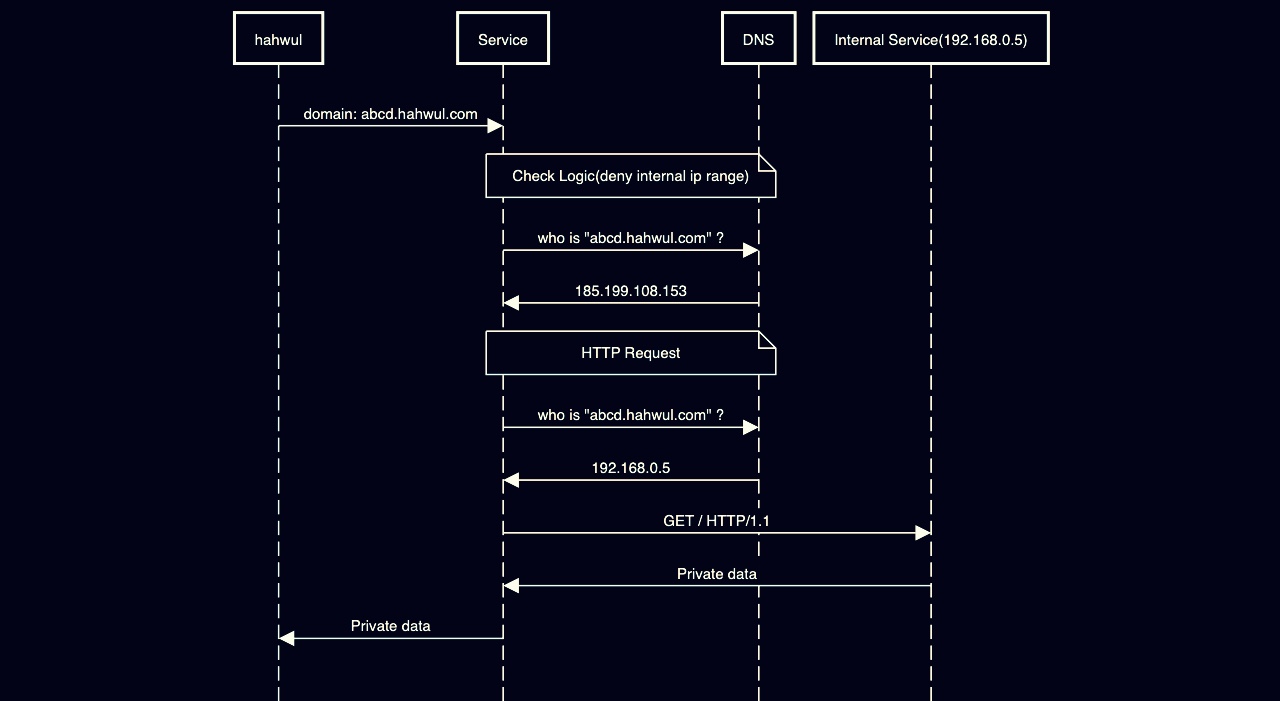
## for https://sequencediagram.org
participant hahwul
participant Service
participant DNS
participant Internal Service(192.168.0.5)
hahwul->Service:domain: abcd.hahwul.com
note over Service,DNS:Check Logic(deny internal ip range)
Service->DNS:who is "abcd.hahwul.com" ?
Service<-DNS:185.199.108.153
note over Service,DNS:HTTP Request
Service->DNS:who is "abcd.hahwul.com" ?
Service<-DNS:192.168.0.5
Service->Internal Service(192.168.0.5):GET / HTTP/1.1
Service<-Internal Service(192.168.0.5):Private data
hahwul<-Service:Private data
Hackerone reports
- SSRF protection bypass in /appsuite/api/oxodocumentfilter addfile action
- GitLab::UrlBlocker validation bypass leading to full Server Side Request Forgery
- Blind HTTP GET SSRF via website icon fetch (bypass of pull#812)
