오늘은 Metasploit 모듈 중 SSL Lab API Client 모듈에 대해 소개해드릴까 합니다.
SSL 평가(취약점-Cipher 지원 등등) 사이트로 유명한 SSLLab(https://www.ssllabs.com )에선 각 도메인에 대한 SSL에 대한 분석 결과 지표를 제공해줍니다.
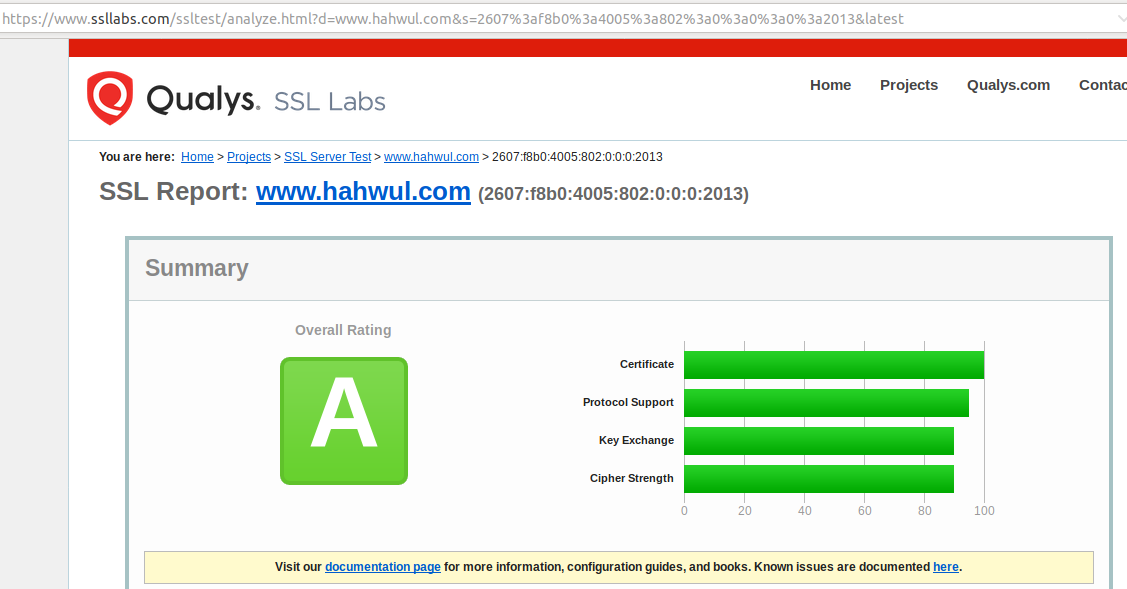
보통은 홈페이지에서 직접 돌리거나 따로 코드짜서 돌리실 것 같은데, 찾다보니 Metasploit 모듈로도 제공되고 있었네요.
HAHWUL (Sessions: 0 Jobs: 0) auxiliary(gather/ssllabs_scan) > search ssl
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/dos/http/sonicwall_ssl_format 2009-05-29 normal SonicWALL SSL-VPN Format String Vulnerability
auxiliary/dos/ssl/dtls_changecipherspec 2000-04-26 normal OpenSSL DTLS ChangeCipherSpec Remote DoS
auxiliary/dos/ssl/dtls_fragment_overflow 2014-06-05 normal OpenSSL DTLS Fragment Buffer Overflow DoS
[…생략…]
auxiliary/gather/ssllabs_scan normal SSL Labs API Client
Options
옵션은 정말 단순합니다. HOSTNAME 정도만 지정해 주시면 됩니다.
HAHWUL (Sessions: 0 Jobs: 0) auxiliary(gather/ssllabs_scan) > show options
Module options (auxiliary/gather/ssllabs_scan):
Name Current Setting Required Description
---- --------------- -------- -----------
DELAY 5 yes The delay in seconds between API requests
GRADE false yes Output only the hostname: grade
HOSTNAME yes The target hostname
IGNOREMISMATCH true yes Proceed with assessments even when the server certificate doesn't match the assessment hostname
USECACHE true yes Use cached results (if available), else force live scan
또한 Advanced도 특별한 건 없습니다.
HAHWUL (Sessions: 0 Jobs: 0) auxiliary(gather/ssllabs_scan) > show advanced
Module advanced options (auxiliary/gather/ssllabs_scan):
Name Current Setting Required Description
---- --------------- -------- -----------
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
Scan
HOSTNAME 세팅 후 돌려주시면 끝납니다. 각각 SSL 취약점 항목부터, Rating 까지 제공해주기 떄문에 결과를 잘 파싱하면 대량의 서비스를 쉽게 돌려볼 수 있을듯 합니다.
HAHWUL (Sessions: 0 Jobs: 0) auxiliary(gather/ssllabs_scan) > set HOSTNAME www.hahwul.com
HOSTNAME => www.hahwul.com
HAHWUL (Sessions: 0 Jobs: 0) auxiliary(gather/ssllabs_scan) > show options
Module options (auxiliary/gather/ssllabs_scan):
Name Current Setting Required Description
---- --------------- -------- -----------
DELAY 5 yes The delay in seconds between API requests
GRADE false yes Output only the hostname: grade
HOSTNAME www.hahwul.com yes The target hostname
IGNOREMISMATCH true yes Proceed with assessments even when the server certificate doesn't match the assessment hostname
USECACHE true yes Use cached results (if available), else force live scan
돌려보면..
HAHWUL (Sessions: 0 Jobs: 0) auxiliary(gather/ssllabs_scan) > run
[*] SSL Labs API info
[*] API version: 1.32.3
[*] Evaluation criteria: 2009p
[*] Running assessments: 0 (max 25)
[*] Server: www.hahwul.com - Resolving domain names
[*] Scanned host: 2607:f8b0:4005:80a:0:0:0:2013 (sfo07s17-in-x13.1e100.net)- 0% complete (Testing Session Ticket support)
[*] Ready: 0, In progress: 1, Pending: 1
[*] www.hahwul.com - Progress 0%
[… 생략 …]
[*] Report for sfo07s13-in-f19.1e100.net (216.58.194.179)
[*] -----------------------------------------------------------------
[+] Overall rating: A
[+] TLS 1.2 - Yes
[+] TLS 1.1 - Yes
[+] TLS 1.0 - Yes
[+] SSL 3.0 - No
[+] SSL 2.0 - No
[+] Secure renegotiation is supported
[!] BEAST attack - Yes
[+] POODLE SSLv3 - Not vulnerable
[+] POODLE TLS - Not vulnerable
[+] Downgrade attack prevention - Yes, TLS_FALLBACK_SCSV supported
[+] Freak - Not vulnerable
[+] RC4 - No
[*] Heartbeat (extension) - No
[+] Heartbleed (vulnerability) - No
[+] OpenSSL CCS vulnerability (CVE-2014-0224) - No
[+] Forward Secrecy - With modern browsers
[+] Strict Transport Security (HSTS) - Yes
[!] Public Key Pinning (HPKP) - No
[+] Compression - No
[*] Session resumption - Yes
[*] Session tickets - No
[*] OCSP Stapling - No
[*] Next Protocol Negotiation (NPN) - Yes (grpc-exp h2 http/1.1)
[*] SNI Required - Yes
[*] Auxiliary module execution completed
이런식으로 결과를 받을 수 있습니다. 웹과 동일하게 Rating A네요 :)

