Apple에서 조만간 iMessage에 PQ3라는 암호화 프로토콜을 적용할 예정이라고 발표했습니다.
개인적으로 PQC1에 관심있었고, 일적으로도 접점이 있어 종종 찾아보곤 헀었는데, 이번 PQ3에 대한 내용은 PQC를 실제로 서비스에 적용하는 경우라서 재미있게 읽었습니다. 덤으로 PQC rekeyring에 대한 내용도 있어 흥미로웠습니다. 오늘은 PQC와 PQ3에 대한 내용으로 간단하게 글 작성해봅니다.
Post-quantum cryptography
Post-quantum cryptography (PQC)는 양자 컴퓨터의 등장으로 기존의 암호 체계가 깨질 가능성에 대비하여 개발된 암호화 방법입니다. 기존의 많은 암호화 방법들, 특히 공개키 암호화 방식은 큰 소수를 소인수분해하는 것이 어렵다는 수학적인 문제를 기반을 두고 있습니다.
이는 컴퓨팅 성능에 밀접하게 영향을 받는데, 양자 컴퓨터가 충분하게 발전한다면 소인수분해 문제를 포함해 기존의 암호화 방식을 깨뜨릴 수 있는 효율적인 알고리즘이 나타날 수 있고 이를 대비하여 개발하는 암호화 로직들을 지칭하는 용어입니다.
PQ3
Key Establishment & Hybrid design
PQ3는 대화 시작부터 PQC를 적용합니다. 초기 키 설정 메커니즘은 Kyber를 통해 발신자가 수신자의 공개 키를 획득하고, 첫 번째 메시지를 위한 post-quantum 암호화 키와 ECC(타원곡선기반) 키 세트를 생성합니다. 참고로 암호화 키 세트는 각 디바이스 별로 만든다고 하네요. (e.g iPhone, Macbook, iPad)
결과적으로 iMessage는 2개의 공개 키를 사용합니다.
- A post-quantum Kyber-1024 key encapsulation public key
- A classical P-256 Elliptic Curve key agreement public key
그리고 이를 통해 암호화 세션 설정 시 각각 공개키로 부터 언어낸 2개의 대칭 키를 모두 사용하여 세션의 암호화에 사용할 초기 키를 만들기 때문에 공격자 입장에선 ECC와 PQC 모두를 깨야 암호화된 데이터를 복호화할 수 있어 전통적인 공격과 양자 암호 공격에 대한 동시 대응이 가능하도록 합니다.
이외에도 ECDSA 서명, Contact Key Verification을 통해 통해 다운그레이드 공격을 방지하고 인증 키와 버전 정보를 검증하는 등 여러가지 보안 요소들이 고려되어 있습니다.
Rekeying Mechanism
PQ3는 rekeying 매커니즘을 가지고 있습니다. rekey를 이용하여 암호화키를 지속적으로 변경하고, 키가 탈취되어도 복호화할 수 있는 메시지의 범위가 제한되기 떄문에 메세지 보안성을 고려하면 높은 수준의 암호 로직을 고려했다고 생각합니다.
Rekeying은 매번 메시지 암호화 시 신규 키를 사용하고 송,수신 마다 암호키를 폐기하는 방식으로 구현된 것 같고, 메시지 사이즈 때문에 일정한 주기? 같은게 설정되어 있는 것 같습니다.
1. 송신자
1-1. 송신자가 메시지 키를 생성한 후 메시지를 암호화하여 전송합니다.
1-2. 메시지 송신 후 암호키를 삭제합니다.
2. 수신자
2-1. 메시지 수신 시 키를 이용해 복호화합니다.
2.2. 복호화 후 암호키를 삭제합니다.
제가 단순하게 표현하였지만 이 과정에선 메시지의 과거, 미래의 보안성을 보장하는 방법 등도 고려되어 있습니다.
Apple’s roadmap?
Apple은 Messaging App에서의 암호화 관련해서 요구되는 내용을 기반으로 Level을 분리해서 관리하는 것 같습니다.
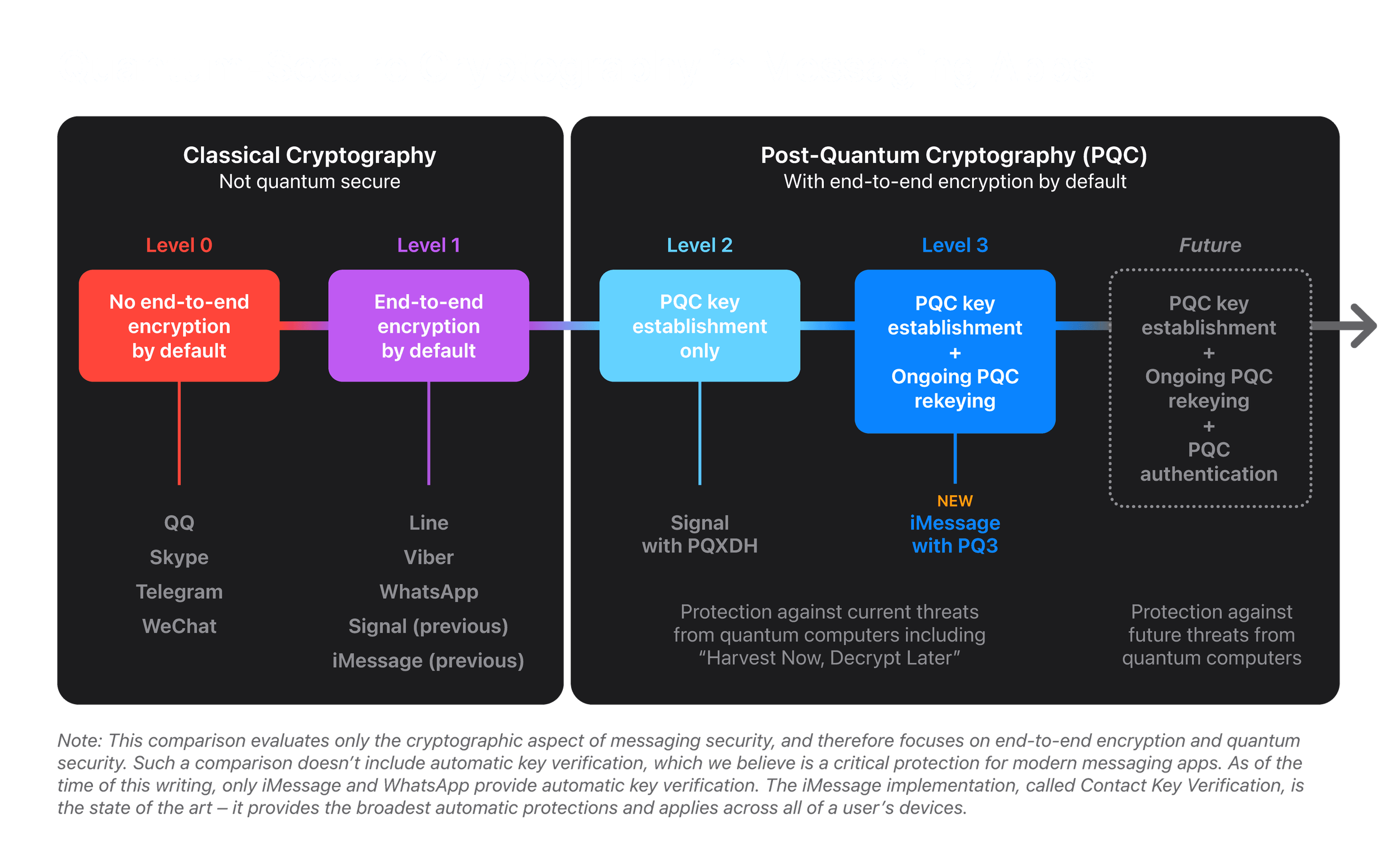 https://security.apple.com/blog/imessage-pq3/
https://security.apple.com/blog/imessage-pq3/
Conclusion
대다수 엔지니어링이 그렇듯이 어떤 결과든 많은 고민과 지식이 함축되어 있다고 생각합니다. 직접적으로 알 수는 없지만 보안성을 위한 설계, 그리고 이를 서비스에 적용하기 까지 걸렸을 노력이 눈에 선하게 보이는 것 같습니다. 요약하다 보니 제 글에는 내용이 많이 빠지게 되었는데, 관심 있으시다면 공식 문서를 꼭 읽어보시는 것을 추천합니다.
References
- https://en.wikipedia.org/wiki/Post-quantum_cryptography
- https://en.wikipedia.org/wiki/Kyber
- https://en.wikipedia.org/wiki/Elliptic-curve_cryptography
- https://security.apple.com/assets/files/Security_analysis_of_the_iMessage_PQ3_protocol_Stebila.pdf
-
Post-quantum cryptography ↩
